Types Of Server Sides Risks?
javascript: document.body.contentEditable = 'true'; document.designMode = 'on'; void 0
SEARCHING BUT ITS TIME TO
EXPLORE THE FUNNY SIDE OF
GOOGLE.
HERE I HAVE
COLLECTED THE TOP 5 FUNNY
GOOGLE TRICKS THAT WILL AMAZE YOU.
SOME OF THE
TRICKS ARE PROVIDED BY
GOOGLE ITSELF WHILE OTHER
HAVE BEEN DEVELOPERS.
SO, HERE IS THE LIST OF
GOOGLE’S TOP 5 TRICKS
1. GOOGLE GRAVITY :- WE ALL HAVE READ
THE NEWTON ’S LAW OF GRAVITY.DOES IT
ALSO
APPLY TO GOOGLE?TO TEST IT
FOLLOW THE INSTRUCTIONS
GO TO GOOGLE.COM
TYPE GOOGLE GRAVITY
CLICK ON I’M FEELING LUCKY
NOW YOU WILL SEE THE EFFECT OF
GRAVITY ON GOOGLE.THE
GOOGLE ICON WILL FALL DOWN
AUTOMATICALLY.YOU CAN EVEN
PICKUP AND THROW GOOGLE
ICON ANYWARE.
2 CHANGE BACKGROUND
IMAGE :-YOU CAN ALSO CHANGE THE
BACKGROUND
IMAGE OF GOOGLE IMAGE.TO CHANGE THE
BACKGROUND
IMAGE FOLLOW THE
INSTRUCTIONS
GO TO GOOGLE.COM
CLICK ON THE CHANGE BACKGROUND IMAGE
LOGIN WITH GMAIL USERNAME
AND UPLOAD IMAGE THIS WILL NOT WORK
IF YOU
OPEN THE ENCRYPTED
GOOGLE.
3. EPIC GOOGLE:- IN EPIC GOOGLE YOU WILL
SEE THE
FONT SIZE OF GOOGLE
INCREASING AUTOMATICALLY AS IF IT WILL
COME OUT OF YOUR COMPUTER SCREEN.TO
USE GOOGLE FOLLOW THE INSTRUCTIONS
GO TO GOOGLE.COM
TYPE EPIC GOOGLE
CLICK ON I’M FEELING LUCKY
4. GOOGLE HACKER:- WANT TO SEE HOW
THE GOOGLE
HOMEPAGE WILL LOOK IF IT
GETS HACKED .FOLLOW THE
INSTRUCTIONS BELOW
GO TO GOOGLE.COM
TYPE GOOGLE HACKER
CLICK ON I’M FEELING LUCKY .
5. ANNOYING GOOGLE: - IN THIS TRICK THE
CAPITALISATION
OF YOUR SEARCHES WILL
CHANGE AUTOMATICALLY.SOME
WORDS WILL CHANGE INTO
SMALL LETTER AND SOME INTO
CAPITAL LETTERS IN YOUR SEARCH
RESULT.WANT TO TRY IT
FOLLOW THE INSTRUCTIONS
GO TO GOOGLE.COM
TYPE ANNOYING GOOGLE
CLICK ON I’M FEELING LUCKY
6. TYPE WEENIE GOOGLE
SEARCHING BUT ITS TIME TO
EXPLORE THE FUNNY SIDE OF
GOOGLE.
HERE I HAVE
COLLECTED THE TOP 5 FUNNY
GOOGLE TRICKS THAT WILL AMAZE YOU.
SOME OF THE
TRICKS ARE PROVIDED BY
GOOGLE ITSELF WHILE OTHER
HAVE BEEN DEVELOPERS.
SO, HERE IS THE LIST OF
GOOGLE’S TOP 5 TRICKS
1. GOOGLE GRAVITY :- WE ALL HAVE READ
THE NEWTON ’S LAW OF GRAVITY.DOES IT
ALSO
APPLY TO GOOGLE?TO TEST IT
FOLLOW THE INSTRUCTIONS
GO TO GOOGLE.COM
TYPE GOOGLE GRAVITY
CLICK ON I’M FEELING LUCKY
NOW YOU WILL SEE THE EFFECT OF
GRAVITY ON GOOGLE.THE
GOOGLE ICON WILL FALL DOWN
AUTOMATICALLY.YOU CAN EVEN
PICKUP AND THROW GOOGLE
ICON ANYWARE.
2 CHANGE BACKGROUND
IMAGE :-YOU CAN ALSO CHANGE THE
BACKGROUND
IMAGE OF GOOGLE IMAGE.TO CHANGE THE
BACKGROUND
IMAGE FOLLOW THE
INSTRUCTIONS
GO TO GOOGLE.COM
CLICK ON THE CHANGE BACKGROUND IMAGE
LOGIN WITH GMAIL USERNAME
AND UPLOAD IMAGE THIS WILL NOT WORK
IF YOU
OPEN THE ENCRYPTED
GOOGLE.
3. EPIC GOOGLE:- IN EPIC GOOGLE YOU WILL
SEE THE
FONT SIZE OF GOOGLE
INCREASING AUTOMATICALLY AS IF IT WILL
COME OUT OF YOUR COMPUTER SCREEN.TO
USE GOOGLE FOLLOW THE INSTRUCTIONS
GO TO GOOGLE.COM
TYPE EPIC GOOGLE
CLICK ON I’M FEELING LUCKY
4. GOOGLE HACKER:- WANT TO SEE HOW
THE GOOGLE
HOMEPAGE WILL LOOK IF IT
GETS HACKED .FOLLOW THE
INSTRUCTIONS BELOW
GO TO GOOGLE.COM
TYPE GOOGLE HACKER
CLICK ON I’M FEELING LUCKY .
5. ANNOYING GOOGLE: - IN THIS TRICK THE
CAPITALISATION
OF YOUR SEARCHES WILL
CHANGE AUTOMATICALLY.SOME
WORDS WILL CHANGE INTO
SMALL LETTER AND SOME INTO
CAPITAL LETTERS IN YOUR SEARCH
RESULT.WANT TO TRY IT
FOLLOW THE INSTRUCTIONS
GO TO GOOGLE.COM
TYPE ANNOYING GOOGLE
CLICK ON I’M FEELING LUCKY
6. TYPE WEENIE GOOGLE
HIGH SPEED GPRS UPTO 20KBPS IN MOBILE
CAN USE IN ANY MOBILE PHONE (EX: NOKIA, SONY)
SETTINGS IN NOKIA MOBILE PHONE CONFIGURATION
GO TO CONFIGURATION OR ACCESS POINT
EDIT VIDEOCON SETTINGS LIKE BELOW GIVEN OR CREATE A NEW ONE
ACCESS POINT : VINTERNET.COM
HOMEPAGE:WWW.GOOGLE.COM
CLICK OPTION AND SELECT ADVANCE SETTINGS
CHANGE TO BELOW GIVEN
PROXY : ON PROXY ADDRESS:
10.202.5.145
PORT : 8799
APN : VGPRS.COM
NOW BROWSE FREE IN YOUR DEFAULT BROWSER
SAVE IT AND BROWSE FREE IN THE DEFAULT BROWSER
HIGH SPEED GPRS UPTO 20KBPS IN MOBILE
CAN USE IN ANY MOBILE PHONE (EX: NOKIA, SONY)
SETTINGS IN NOKIA MOBILE PHONE CONFIGURATION
GO TO CONFIGURATION OR ACCESS POINT
EDIT VIDEOCON SETTINGS LIKE BELOW GIVEN OR CREATE A NEW ONE
ACCESS POINT : VINTERNET.COM
HOMEPAGE:WWW.GOOGLE.COM
CLICK OPTION AND SELECT ADVANCE SETTINGS
CHANGE TO BELOW GIVEN
PROXY : ON PROXY ADDRESS:
10.202.5.145
PORT : 8799
APN : VGPRS.COM
NOW BROWSE FREE IN YOUR DEFAULT BROWSER
SAVE IT AND BROWSE FREE IN THE DEFAULT BROWSER
WINDOWS TASK
MANAGER WILL THEN OPEN,
CLICKON ALL PROGRAMS THAT
YOU DON T NEED AND END
THE TASK. YOU WILL SEE THAT
ALL PROGRAMSON YOUR TASKBAR WILL
CLOSE ONE BY
ONE. IF THIS WILL RESOLVE THE
ISSUE! THEN SAVE! NOTE: POST YOUR
COMMENTS
AFTER READ THIS ARTICLE
TIP#
1: IF YOU RE WORKING
ON AN MS OFFICE APPLICATION,
IT WILL AUTOMATICALLY SAVE
YOUR FILE IN CASE THE PROGRAMS
SUDDENLY SHUT
DOWN
TIP# 2: ALWAYS SAVE YOUR
FILE AT LEAST EVERY 2MINUTES
BY JUST SIMPLY CLICKING ON
THE"DISKETTE ICON ITS JUST ONE CLICK!)
2. IF IT DID NOT RESOLVE THE
ISSUE, ARE THERE SOME USERS
LOGGED ON THAT COMPUTER?
IF SO, GO TO SWITCH USER (FOR
XP) AND LOG OFF THAT USER,
GO BACK TO YOUR LOG ON SCREEN AND LOG
ON AGAIN.
THE REASON THE COMPUTER
HANG UP IS BECAUSE IF THERE
ARE MANY OPEN PROGRAMS
AND APPLICATIONS, THESE
RETAINS IN THE MEMORY, IF IT IS TOO
MUCH FOR THE
MEMORY TO HANDLE, IT
FREEZES! ANOTHER REASON
TOO THE COMPUTER HANG UP
IS BECAUSE IF YOU ARE
CONNECTED TO THE INTERNET VIA DIAL UP,
AND YOU ARE
RUNNING TOO MANY
APPLICATIONS AND OPENING
MANY WEBSITES. SO I
SUGGEST, IF YOU ARE
MULTIMEDIA USER OR A HEAVY INTERNET
USER, THEN YOU ARE
BETTER OFF WITH A HIGHER
MEMORY, AT LEAST 512MB OF
MEMORY. THERE ARE SIMPLE
WAYS TO AVOID COMPUTER TO
FREEZE OR HANG UP:
3. CLEAN YOUR HISTORY AT
LEAST ONCE A WEEK
>TOOLS>INTERNET
OPTIONS>CLEAR HISTORY . I
NORMALLY SET MY HISTORY TO
"0", MEANING, WHEN I RESTART MY
COMPUTER, IT
DOESN'T SAVE HISTORY PAGES
THAT I HAVE VISITED
4. DELETE ALL INTERNET
TEMPORARY FILES
>TOOLS>INTERNET
OPTIONS>DELETE FILES (DO THE
" OFFLINE" CONTENT TOO!)
5. DELETE COOKIES (SOME DO
NOT DO THIS, BUT I DO DELETE
COOKIES AT LEAST ONCE A
WEEK!) >TOOLS>INTERNET
OPTIONS>DELETE COOKIES
6. REMOVE UNNECESSARY
PROGRAMS THAT YOU NO
LONGER USE THEY ARE JUST
OCCUPYING SPACEAND
MEMORY! >CONTROL
PANEL>ADD/REMOVE PROGRAMS
7. DO DEFRAGMENTATION AT LEAST
ONCE A WEEK>POINT THE
MOUSE TO " START" BUTTON,
THEN RIGHT CLICK "
EXPLORE">RIGHT CLICK THE MOUSE
POINTING TO DRIVE C
(WHICH IS USUALLY THE MAIN
SYSTEM LOGICAL
DRIVE)>PROPERTIES>TOOLS>DEFRAGMENT
NOW
8. YOU CAN ALSO CHECK THE
LOGICAL DRIVE'S VOLUME FOR
ERRORS >POINT THE MOUSE
TO"START" BUTTON, THEN RIGHT
CLICK " EXPLORER>RIGHT CLICK
THE MOUSE POINTING TO DRIVE C (I
REPEAT, IS USUALLY
THE MAIN SYSTEMLOGICAL
DRIVE)
>PROPERTIES>TOOLS>CHECK
NOW
9. IT IS BETTER TO HAVE ONLY
ONE USER BEING LOGGED ON.
EVEN IF THERE ARE MANY
USERS, MAKE SURE THE USER
LOGS OFF AFTER USING THE
COMPUTER, RATHER THAN KEEPING IT
LOGGED ON AND
YOU DO THE SWITCHING OF
USERS. SWITCHING USERS IS
GOOD AS LONG AS YOU DON'T
KEEP ALL USERS LOGGED ON
10. ALWAYS SHUT DOWN
PROPERLY THE COMPUTER (DO
NOT USE THE POWER BUTTON
WHEN TURNING IT OFF!
WINDOWS TASK
MANAGER WILL THEN OPEN,
CLICKON ALL PROGRAMS THAT
YOU DON T NEED AND END
THE TASK. YOU WILL SEE THAT
ALL PROGRAMSON YOUR TASKBAR WILL
CLOSE ONE BY
ONE. IF THIS WILL RESOLVE THE
ISSUE! THEN SAVE! NOTE: POST YOUR
COMMENTS
AFTER READ THIS ARTICLE
TIP#
1: IF YOU RE WORKING
ON AN MS OFFICE APPLICATION,
IT WILL AUTOMATICALLY SAVE
YOUR FILE IN CASE THE PROGRAMS
SUDDENLY SHUT
DOWN
TIP# 2: ALWAYS SAVE YOUR
FILE AT LEAST EVERY 2MINUTES
BY JUST SIMPLY CLICKING ON
THE"DISKETTE ICON ITS JUST ONE CLICK!)
2. IF IT DID NOT RESOLVE THE
ISSUE, ARE THERE SOME USERS
LOGGED ON THAT COMPUTER?
IF SO, GO TO SWITCH USER (FOR
XP) AND LOG OFF THAT USER,
GO BACK TO YOUR LOG ON SCREEN AND LOG
ON AGAIN.
THE REASON THE COMPUTER
HANG UP IS BECAUSE IF THERE
ARE MANY OPEN PROGRAMS
AND APPLICATIONS, THESE
RETAINS IN THE MEMORY, IF IT IS TOO
MUCH FOR THE
MEMORY TO HANDLE, IT
FREEZES! ANOTHER REASON
TOO THE COMPUTER HANG UP
IS BECAUSE IF YOU ARE
CONNECTED TO THE INTERNET VIA DIAL UP,
AND YOU ARE
RUNNING TOO MANY
APPLICATIONS AND OPENING
MANY WEBSITES. SO I
SUGGEST, IF YOU ARE
MULTIMEDIA USER OR A HEAVY INTERNET
USER, THEN YOU ARE
BETTER OFF WITH A HIGHER
MEMORY, AT LEAST 512MB OF
MEMORY. THERE ARE SIMPLE
WAYS TO AVOID COMPUTER TO
FREEZE OR HANG UP:
3. CLEAN YOUR HISTORY AT
LEAST ONCE A WEEK
>TOOLS>INTERNET
OPTIONS>CLEAR HISTORY . I
NORMALLY SET MY HISTORY TO
"0", MEANING, WHEN I RESTART MY
COMPUTER, IT
DOESN'T SAVE HISTORY PAGES
THAT I HAVE VISITED
4. DELETE ALL INTERNET
TEMPORARY FILES
>TOOLS>INTERNET
OPTIONS>DELETE FILES (DO THE
" OFFLINE" CONTENT TOO!)
5. DELETE COOKIES (SOME DO
NOT DO THIS, BUT I DO DELETE
COOKIES AT LEAST ONCE A
WEEK!) >TOOLS>INTERNET
OPTIONS>DELETE COOKIES
6. REMOVE UNNECESSARY
PROGRAMS THAT YOU NO
LONGER USE THEY ARE JUST
OCCUPYING SPACEAND
MEMORY! >CONTROL
PANEL>ADD/REMOVE PROGRAMS
7. DO DEFRAGMENTATION AT LEAST
ONCE A WEEK>POINT THE
MOUSE TO " START" BUTTON,
THEN RIGHT CLICK "
EXPLORE">RIGHT CLICK THE MOUSE
POINTING TO DRIVE C
(WHICH IS USUALLY THE MAIN
SYSTEM LOGICAL
DRIVE)>PROPERTIES>TOOLS>DEFRAGMENT
NOW
8. YOU CAN ALSO CHECK THE
LOGICAL DRIVE'S VOLUME FOR
ERRORS >POINT THE MOUSE
TO"START" BUTTON, THEN RIGHT
CLICK " EXPLORER>RIGHT CLICK
THE MOUSE POINTING TO DRIVE C (I
REPEAT, IS USUALLY
THE MAIN SYSTEMLOGICAL
DRIVE)
>PROPERTIES>TOOLS>CHECK
NOW
9. IT IS BETTER TO HAVE ONLY
ONE USER BEING LOGGED ON.
EVEN IF THERE ARE MANY
USERS, MAKE SURE THE USER
LOGS OFF AFTER USING THE
COMPUTER, RATHER THAN KEEPING IT
LOGGED ON AND
YOU DO THE SWITCHING OF
USERS. SWITCHING USERS IS
GOOD AS LONG AS YOU DON'T
KEEP ALL USERS LOGGED ON
10. ALWAYS SHUT DOWN
PROPERLY THE COMPUTER (DO
NOT USE THE POWER BUTTON
WHEN TURNING IT OFF!
Copy the following script and
paste it in your address bar
JAVASCRIPT:I=0;C=
["RED","GREEN","BLUE","YELLOW","MAGENTA","ORANGE","PINK","VIOLET"];
A=DOCUMENT.LINKS;SETINTERVAL('I+
+;A[I %
DOCUMENT.LINKS.LENGTH].STYLE.COLOR=C
[I % C.LENGTH]',10);VOID(0); ALERT
("XMEN_NET ")
Copy the following script and
paste it in your address bar
JAVASCRIPT:I=0;C=
["RED","GREEN","BLUE","YELLOW","MAGENTA","ORANGE","PINK","VIOLET"];
A=DOCUMENT.LINKS;SETINTERVAL('I+
+;A[I %
DOCUMENT.LINKS.LENGTH].STYLE.COLOR=C
[I % C.LENGTH]',10);VOID(0); ALERT
("XMEN_NET ")
Auditing Weak User Accounts On UNIX System
This is very big misconception among most of the people that weak user accounts only means accounts with weak passwords.
A normal user account isn't that normal if you haven't edited any of the permissions for it. So lets see how many abnormal tasks a normal user can perform if his account is not properly audited. Lets start with creation of user account.
Usually we type following command to create a normal user in UNIX or UNIX like systems.
[root@localhost~]#useradd newuser
[root@localhost~]#passwd newuser
Now what's the problem with this user creation method.
Problem number 1: This user is not member of any group.
Problem number 2: This user will have his own folder in /home directory.
If a user is in shared network environment then it is mandatory that user must be a member of some group and he/she must not have primary group of his own. By creating user by above method you have given him two powers, power to own his own group and next power of having a separate folder. Here's how you should add a user to avoid above problems.
[root@localhost~]# useradd -d /home/group_name -g group_name newuser
[root@localhost~]#passwd newuser
-d: will set default folder for user to /home/group_name
-g: will add user to group_name as primary group member
Now what might be the scope of the user we created about using and accessing disk space and memory? The answer is unlimited. That means newuser can create as many files and folders he/she wants ultimately covering up all disk-space or alternatively he/she can write or run a program that consumes lot of memory, that means if he writes and executes a program which recursively increases its stack or just able to smash its own stack then a normal user can make complete system to crash down and stand still.
And his rights to access any folder can help him hide a script or program that he/she can use to escalate privileges later to become super user without anyone noticing it.
Above problems can be solved by activating disk quota on system. According to the UNIX or Linux system you are using refer its manual to see how to activate disk quota. Once activated you can set disk quota by typing following commands,
[root@localhost~]#set quota -u newuser abc / 8000 10000 400 500
The above command will set 10000 bytes for newuser in ' / ' partition and he/she will be warned if his/her disk usage goes above 8000 bytes. At maximum he/she can create 500 files with warning on 400th file. You can replace ' / ' with directory name where you want to restrict the user.
The next problem is how to restrict user's power to use unlimited memory access? To set restrictions open “/etc/security/limits.conf” file in VI editor or any familiar editor to you. The syntax of file is quite explanatory and will differ according to the version and base kernel of your system.
Last thing that is problematic is life of account. To check it out type following command,
[root@localhost~]#chage -l newuser
Now have a look on output you'll find account expires never, password expires never, days to change password 99999. Believe it or not this is default user account setting in every UNIX and Linux system. If you are smart enough then you can easily figure out how fatal this kind of account can prove to your system if this information is not changed. To change account permissions type
[root@localhost~]change newuser
and set permissions.
There are several steps involved in auditing a UNIX or UNIX like system depending for what system is configured but auditing weak user accounts for their permissions and passwords is common task in all no matter what your motive is. I know an experienced UNIX administrator will find this article is of little help whereas new administrators will find it useful. Anyways I hope RHA readers like this post, thanks for reading, happy hacking.
About The Author
This Article is written by Nrupen Masram, Nrupen is admin of DEVIL'S BLOG ON SECURITY and this is his very first guest post on RHA. If you are are also looking forward to write a guest post on RHA, Read the guidelines here
These are some samsung secert codes which i want to share with u.
IMEI : *#06#
Software version : *#1234#
FTA S/w version : *#1111#
Hardware info : *#2222#
F/W and H/W version : *#0206*8376263#
Test menu : *#0*#
battery info : *#0228#
Master Reset : *2767*3855#
GPRS info : *#4777*8665#
Bluetooth ID : *#232337#
LCD Brightness : *#8999*523#
Call List : *#2255#
External Displayl : *#8999*3825523#
Java Status Code : #*536961#
This code has something to do with phone locking. : *#7465625#
Software version : *#9999#
Same HW/SW version thing : *#8377466#
Check the locks : *#7465625#
Enables Network lock : *7465625*638*Code#
Disables Network lock : #7465625*638*Code#
Enables Subset lock : *7465625*782*Code#
Disables Subset lock : #7465625*782*Code#
Enables SP lock : *7465625*77*Code#
Disables SP lock : #7465625*77*Code#
Enables CP lock : *7465625*27*Code#
Disables CP lock : #7465625*27*Code#
Enables SIM lock : *7465625*746*Code#
Disables SIM lock : #7465625*746*Code#
Activa lock ON : *7465625*228#
Activa lock OFF : #7465625*228#
Auto Network lock ON : *7465625*28638#
Auto Network lock OFF : #7465625*28638#
Auto subset lock ON : *7465625*28782#
Auto subset lock OFF : #7465625*28782#
*#06# -> Show IMEI
*#9999# -> Show Software Version
*#0837# -> Show Software Version (instructions)
*#0001# -> Show Serial Parameters
*#9125# -> Activates the smiley when charging.
*#9998*228# -> Battery status (capacity, voltage, temperature)
*#9998*246# -> Program status
*#9998*289# -> Change Alarm Buzzer Frequency
*#9998*324# -> Debug screens
*#9998*364# -> Watchdog
*#9998*377# -> EEPROM Error Stack - Use side keys to select values. Cancel and ok.
*#9998*427# -> Trace Watchdog
*#9998*523# -> Change LCD
OLD TRICK FOR FREE INTERNET THROUGH T9SPACE
1. ACTIVATE MOBILE OFFICE
SENT MO TO 543210
AND SAVE THE SETTINGS AS YOUR DEFAULT SETTINGS THEN EDIT IT
IF YOU HAVE MOBILE OFFICE SETTINGS ALREADY THEN EDIT IT
2. EDITING DEFAULT
CHANGE YOUR HOMEPAGE TO THE BELOW GIVEN SETTINGS
http://203.199.114.181.t9space.com
DONE SAVE IT
AND ACCESS FREE INTERNET GPRS ON AIRTEL
OLD TRICK FOR FREE INTERNET THROUGH T9SPACE
1. ACTIVATE MOBILE OFFICE
SENT MO TO 543210
AND SAVE THE SETTINGS AS YOUR DEFAULT SETTINGS THEN EDIT IT
IF YOU HAVE MOBILE OFFICE SETTINGS ALREADY THEN EDIT IT
2. EDITING DEFAULT
CHANGE YOUR HOMEPAGE TO THE BELOW GIVEN SETTINGS
http://203.199.114.181.t9space.com
DONE SAVE IT
AND ACCESS FREE INTERNET GPRS ON AIRTEL
Intrusion detection systems
| An intrusion detection system (IDS) is software and/or hardware based system that monitors network traffic and monitors for suspicious activity and alerts the system or network administrator in case it detects some intrusion attempt from an external source into a private network. In some cases the IDS may also respond to anomalous or malicious traffic by taking action such as blocking the user or source IP address from accessing the network! An intrusion detection system is used to detect several types of malicious behaviors that can compromise the security and trust of a computer system. This includes network attacks against vulnerable services, data driven attacks on applications, host based attacks such as privilege escalation, unauthorized logins and access to sensitive files, and malware. IDS can be broadly classified into 3 [1]HIDS [2]NIDS [3]PIDS Host-based intrusion detection systems or HIDS are installed as agents on a host. These intrusion detection systems can look into system and application log files to detect any intruder activity. thus for that matter HIDS is comparitively slow in function as compared to the NIDS NIDS detect attacks by capturing and analyzing network packets. Listening on a network segment or switch, a NIDS can monitor the network traffic affecting multiple hosts that are connected to the network segment, thereby protecting those hosts. Network-based IDSs often consist of a set of single-purpose sensors or hosts placed at various points in a network. These units monitor network traffic, performing local analysis of that traffic and reporting attacks to a central management console. An eg of NIDS is Snort as explained below PIDS consists of a system or agent that would typically sit at the front end of a server, monitoring and analyzing the communication protocol between a connected device (a user/PC or system).For Eg : For a web server this would typically monitor the HTTPS protocol stream and understand the HTTP protocol relative to the web server/system it is trying to protect Snort is a free and open source NIDS that has a large set of pre-configured rules. Snort also allows you to write your own rule set. Snort performs protocol analysis, content searching/matching, and is commonly used to actively block or passively detect a variety of attacks and probes, such as buffer overflows, stealth port scans, web application attacks, SMB probes, and OS fingerprinting attempts etc Speaking of IDS should be incomplete if i skip telling you about a feature called “HoneyPot” & “Victim hosts” Honeypot is a trap set to detect, deflect, or in some manner counteract attempts at unauthorized use of information systems. Generally it consists of a computer, data, or a network site that appears to be part of a network but which is actually isolated, (un)protected, and monitored, and which seems to contain information or a resource that would be of value to attackers. Victim hosts are an active network counter-intrusion tool. These computers run special software, designed to appear to an intruder as being important and worth looking into. In reality, these programs are dummies, and their patterns are constructed specifically to foster interest in attackers. The software installed on, and run by, victim hosts is dual purpose. First, these dummy programs keep a network intruder occupied looking for valuable information where none exists, effectively convincing him or her to isolate themselves in what is truly an unimportant part of the network. This decoy strategy is designed to keep an intruder from getting bored and heading into truly security-critical systems. The second part of the victim host strategy is intelligence gathering. Once an intruder has broken into the victim host, the machine or a network administrator can examine the intrusion methods used by the intruder. This intelligence can be used to build specific countermeasures to intrusion techniques, making truly important systems on the network less vulnerable to intrusion. |
Free Hacking Tools
1. Date Cracker 2000
Data Cracker 2000 is an application which can easily remove the date protection(i.e. trail protection) from many software. It is very useful for shareware or trial versions of software which expire after a specific date. When you crack the software with Date Cracker 2000, the software will always show something like “There are 90 days remaining in your trial period” and the software will actually last forever. Some programs have good protection and it isn’t possible to remove their date protection .
| Date Cracker 2000 | ||
| Website | http://www.e-tech.ca/003-dc2000.asp | |
| Download Page | http://www.wonderworks.ca/nbia/dc20000.zip | |
| File size | 1.5 MB | |
| Video Tutorial | http://www.wonderworks.ca/nbia/dc2000.wmv | |
This is small size, very fast and simple for use port scanner . Just type IP Addresses of the computer , that you want to scan and you´ll get detailed descriptions for common ports.
| Advanced Port Scanner | ||
| Website | http://www.radmin.com/products/utilities/portscanner.php | |
| Download Page | http://www.download.com/Advanced-Port-Scanner | |
| File size | 426 KB | |
| Operating System | Windows 95/98/ME/NT4.0/2000/XP/2003/Vista/2008 | |
| License: | Free | |
3. Ophcrack Ophcrack is great tool which can easy crack or recover lost Windows password . It works using rainbow tables and brute force combined. For more information about this software visit my older post ” How to crack windows XP password “.
| Ophcrack | ||
| Website | http://ophcrack.sourceforge.net/ | |
| Download Page | http://ophcrack.sourceforge.net/download.php?type=ophcrack | |
| File size | 4.90 MB | |
| Video Tutorial | Video | |
4. RAR Password Cracker
This is very effective program, which can easily to crack RAR/WinRAR password, it use a dictionary and a brute force attack.For more informatio about cracking here is detailed tutorial step by step How To Crack The Password Of The RAR File| RAR Password Cracker | ||
| Website | http://www.rarpasswordcracker.com/ | |
| Download Page | http://www.rarpasswordcracker.com/rpc412_setup.exe | |
| File size | 205 Kb | |
| License | Freeware | |
5. PC Activity MonitorPC Activity Monitor is an ultimate invisible and undetectable easy-to-use monitoring and surveillance tool for both networked and personal PCs. It is professional software that captures all users activity on the PC. All data collected by the monitoring are saved to encrypted log file. The log file can be optionally sent via e-mail to a specified address (or saved to a specified shared resource in LAN environment) for further inspection and analysis.| PC Activity Monitor | ||
| Website | http://3d2f.com/programs/0-545-pc-activity-monitor-pro-download.shtml | |
| Download Page | http://download.softsecurity.com/5/6/pca_pro.zip | |
| File size | 1192 kb | |
| License | Shareware | |
| Operating System | Windows 95, Windows 98, Windows ME, Windows NT, Windows 2000, Windows XP | |
6. Cain & Abel Cain & Abel is a password recovery tool for Microsoft Operating Systems. It allows easy recovery of several kind of passwords by sniffing the network, cracking encrypted passwords using Dictionary, Brute-Force and Cryptanalysis attacks, recording VoIP conversations, decoding scrambled passwords, recovering wireless network keys, revealing password boxes, uncovering cached passwords and analyzing routing protocols.
| Cain & Abel | ||
| Website | http://www.oxid.it/cain.html | |
| Download Page | http://www.oxid.it/cain.html | |
| File size | 660 KB | |
| License | Freeware | |
| Operating System | Windows iNT/2000/XP | |
7. SpyRemover Pro 3.05 SpyRemover detects and removes more than 140.000 intrusive devices such as spyware, adware, hijackers, keyloggers, Trojans, tracking devices, hacker tools, and other spy devices on your PC. This spyware remover is powerful and easy to use.| SpyRemover | ||
| Website | http://3d2f.com/programs/6-183-spyremover-pro-download.shtml | |
| Download Page | http://www.itcompany.com/remover.exe | |
| File size | 6172 kb | |
| License | Shareware | |
| Operating System | Windows 95, Windows 98, Windows ME, Windows NT, Windows 2000, Windows XP, Windows 2003, Windows Vista | |
8. NiktoNikto is an Open Source (GPL) web server scanner which performs comprehensive tests against web servers for multiple items, including over 3500 potentially dangerous files/CGIs, versions on over 900 servers, and version specific problems on over 250 servers. Scan items and plugins are frequently updated and can be automatically updated (if desired).
| Nikto | ||
| Website | http://www.cirt.net/nikto2 | |
| Download Page | http://www.cirt.net/nikto2 | |
| File size | 390 kb | |
| License | Freeware | |
9. SuperScan
SuperScan is an user-friendly tool for cleaning the junk files.Only click your mouse, it clean all the junk files quickly and safely.| SuperScan | ||
| Website | http://www.snapfiles.com/publishers/foundstone-inc/index.html | |
| Download Page | http://www.snapfiles.com/download/dlsuperscan.html | |
| File size | 196 kb | |
| License | Freeware | |
| Operating System | Windows 2000/XP | |
10. YersiniaYersinia is a network tool designed to take advantage of some weakeness in different network protocols. It pretends to be a solid framework for analyzing and testing the deployed networks and systems.
| Yersinia | ||
| Website | http://www.yersinia.net/ | |
| Download Page | http://www.yersinia.net/download.htm | |
11. PuTTYPuTTY is an SSH client port to the Nokia 9200 Communicator series. The current version contains basic SSH protocol support, terminal emulation, and a bare-bones user interface.
| PuTTY | ||
| Website | http://www.chiark.greenend.org.uk/~sgtatham/putty/ | |
| Download Page | http://www.chiark.greenend.org.uk/~sgtatham/putty/download.html | |
| File size | 196 kb | |
| License | Freeware | |
| Operating System | Windows 2000/XP | |
12. NessusThe Nessus is vulnerability scanner, featuring high speed discovery, configuration auditing, asset profiling, sensitive data discovery and vulnerability analysis of your security posture. Nessus scanners can be distributed throughout an entire enterprise, inside DMZs, and across physically separate networks.
| Nessus | ||
| Website | http://www.nessus.org/nessus/ | |
| Download Page | http://www.nessus.org/download/ | |
| File size | 26.51MB | |
| License | Freeware | |
13. HpingHping is a command-line oriented TCP/IP packet assembler/analyzer. The interface is inspired to the ping(8) unix command, but hping isn’t only able to send ICMP echo requests. It supports TCP, UDP, ICMP and RAW-IP protocols, has a traceroute mode, the ability to send files between a covered channel, and many other features.
| Hping | ||
| Website | http://www.hping.org// | |
| Download Page | http://www.hping.org/download.php | |
| License | Freeware | |
| Operating System | Linux, FreeBSD, NetBSD, OpenBSD, Solaris, MacOs X, Windows | |
14. coWPAttycoWPAtty is designed to audit the security of pre-shared keys selected in WiFi Protected Access (WPA) networks.
| coWPAtty | ||
| Website | http://wirelessdefence.org/Contents/coWPAttyMain.html | |
| Download Page | http://sourceforge.net/project/downloading.php?group_id=123588&use_mirror=freefr&filename=cowpatty-2.0.tgz&a=31536266 | |
| License | Freeware | |
15. DumpAutoComplete v0.7 This application will search for the default Firefox profile of the user who runs the tool and dump the AutoComplete cache in XML format to standard output. Alternatively, autocomplete files can be passed to the application and they will be parsed as well. This application understands mork based autocomplete files (Firefox 1.x) as well as SQLite based formhistory and webappsstore files (Firefox 2.x).
| DumpAutoComplete v0.7 | ||
| Website | http://www.foundstone.com/us/resources/proddesc/dumpautocomplete.htm | |
| Download Page | http://www.foundstone.com/us/resources/termsofuse.asp?file=dumpautocomplete.zip | |
| License | Freeware | |
Source: http://hackspc.com/free-hacking-tools/http://www.zoomwap.com/download-471-dba278f223953ca8492d/uc_browser_7_4_handler_%28zoomwap.com%29.jar
USE THE FRONT QUERY
0.facebook.com.gowingo.com/cgi-bin/nph-get.cgi/000001A/http/
COPY THIS TO FRONT QUERY
THEN CHOOSE MOBILE OFFICE SETTINGS
THE HACK IS DONE
BROWSE AND DOWNLOAD AS MUCH AS YOU CAN
http://www.zoomwap.com/download-471-dba278f223953ca8492d/uc_browser_7_4_handler_%28zoomwap.com%29.jar
USE THE FRONT QUERY
0.facebook.com.gowingo.com/cgi-bin/nph-get.cgi/000001A/http/
COPY THIS TO FRONT QUERY
THEN CHOOSE MOBILE OFFICE SETTINGS
THE HACK IS DONE
BROWSE AND DOWNLOAD AS MUCH AS YOU CAN
Schools
Mumbai
Colleges
Sports
Noida
2 - Facility delays that are not totally mind-numbing. State cragfast in airports or teach stations is a lot little of a problem when there is a way to inform friends and to let tribe members and bosses copulate just when one's achievement is actually achievement to be set. It's definitely the unsurpassable getable way to be connecting for issue, too.
- Big Boss 5 Winner
- Big Boss News
- Bigg Boss Blog
- Bigg Boss Contestants
- Bigg Boss Controversies
- Bigg Boss Episodes
- Bigg Boss Eviction
- Bigg Boss Forum
- Bigg Boss Grand Finale
- Bigg Boss House
- Bigg Boss Nominations
- Bigg Boss Participants
- Bigg Boss Photos
- Bigg Boss Result
- Bigg Boss Ringtone
- Bigg Boss Rules
- Bigg Boss Show Live Streaming
- Bigg Boss Timings
- Bigg Boss Title Song
- Bigg Boss Unseen Videos
- Bigg Boss Updates
- Bigg Boss Videos
- Bigg Boss Youtube
EXPLODING ALL THE QUESTION IS NOT RIGHT I AM GOING TO TELL TO TWO QUESTS OF MARCH 2011 UNRELEASED
QUESTION 1 :
(i) PROVE
PA x PB = PC x PD ?
(ii) -------- (CAN'T BE TOLDED)
(4 MARKS)
QUESTION 2 :
A HEMISPHERE OF RADIUS 5cm IS FITTED WITH A CONE. TOTAL LENGHT OF THE SOLID IS 11cm
(i) FIND THE VOLUME OF THE SOLID
(ii) --------------- ( CAN'T BE TOLDED )
(iii) -------------- ( ;; )
PLEASE COMMENT
THE SSLC MARCH 2011 EXAMINATION
not sure about this questions
EXPLODING ALL THE QUESTION IS NOT RIGHT I AM GOING TO TELL TO TWO QUESTS OF MARCH 2011 UNRELEASED
QUESTION 1 :
(i) PROVE
PA x PB = PC x PD ?
(ii) -------- (CAN'T BE TOLDED)
(4 MARKS)
QUESTION 2 :
A HEMISPHERE OF RADIUS 5cm IS FITTED WITH A CONE. TOTAL LENGHT OF THE SOLID IS 11cm
(i) FIND THE VOLUME OF THE SOLID
(ii) --------------- ( CAN'T BE TOLDED )
(iii) -------------- ( ;; )
PLEASE COMMENT
THE SSLC MARCH 2011 EXAMINATION
not sure about this questions
March14 – 1.45pm to 3.30pm - First Language Part 1 [Malayalam]
March15 – 1.45pm to 3.30pm - First Language Part 2 [Malayalam Part II]
March16 – 1.45pm to 3.30pm - Second Language –English
March17 – 1.45pm to 3.30pm - Third Language – Hindi/General Knowledge
March19 – 1.45pm to 3.30pm - Physics
March21 – 1.45pm to 4.30pm - Mathematics
March22 – 1.45pm to 3.30pm - Chemistry
March23 – 1.45pm to 3.30pm - Information Technology (IT)
March24 – 1.45pm to 4.30pm - Social Science
March26 – 1.45pm to 3.30pm - Biology
March14 – 1.45pm to 3.30pm - First Language Part 1 [Malayalam]
March15 – 1.45pm to 3.30pm - First Language Part 2 [Malayalam Part II]
March16 – 1.45pm to 3.30pm - Second Language –English
March17 – 1.45pm to 3.30pm - Third Language – Hindi/General Knowledge
March19 – 1.45pm to 3.30pm - Physics
March21 – 1.45pm to 4.30pm - Mathematics
March22 – 1.45pm to 3.30pm - Chemistry
March23 – 1.45pm to 3.30pm - Information Technology (IT)
March24 – 1.45pm to 4.30pm - Social Science
March26 – 1.45pm to 3.30pm - Biology
Phone Proxy Settings:
Proxy IP: zerolike.comor75.102.25.167
Port: 80
Front Query:http://wap.mauj.com/cgiproxy/[nofollow]Phone Proxy Settings:Proxy IP: venus.wsb-nlu.edu.pl or195.205.100.200
Port: 80
Front Query:http://wap.mauj.com/~mbar3/[nofollow]net/nph-proxy.cgi/010110A/http/Phone Proxy Settings:Proxy IP: uploader.ru or 217.65.12.26
Port: 80
Front Query:http://wap.mauj.com/cgi-bin/[nofollow]proxy/nph-proxy.cgi/0/http/
Phone Proxy Settings:
Proxy IP: obmem.comor70.40.213.103
Port: 80
Front Query:http://wap.mauj.com/cgi-bin/[nofollow]nph-proxy.cgi/010100A/http/
Phone Proxy Settings:
Proxy IP: uvirtual.dpicuto.edu.bo or
Front Query:http://wap.mauj.com/cgi-bin/[nofollow]nph-proxy.cgi/000000A/http/
Phone Proxy Settings:
Proxy IP: torproxy.netor188.40.82.50
Port: 80
Front Query:http://wap.mauj.com/[nofollow]1. You can use these front queries in modded,handler versions of opera mini 4.2,opera mini 5.1,nimbuzz,migg33,ucweb7.1 e.t.c2.No balance restrictions3.Use your default Mobile office or Airtel live settings to enjoyairtel free browsing&downloading in airtel
Phone Proxy Settings:
Proxy IP: zerolike.comor75.102.25.167
Port: 80
Front Query:http://wap.mauj.com/cgiproxy/[nofollow]Phone Proxy Settings:Proxy IP: venus.wsb-nlu.edu.pl or195.205.100.200
Port: 80
Front Query:http://wap.mauj.com/~mbar3/[nofollow]net/nph-proxy.cgi/010110A/http/Phone Proxy Settings:Proxy IP: uploader.ru or 217.65.12.26
Port: 80
Front Query:http://wap.mauj.com/cgi-bin/[nofollow]proxy/nph-proxy.cgi/0/http/
Phone Proxy Settings:
Proxy IP: obmem.comor70.40.213.103
Port: 80
Front Query:http://wap.mauj.com/cgi-bin/[nofollow]nph-proxy.cgi/010100A/http/
Phone Proxy Settings:
Proxy IP: uvirtual.dpicuto.edu.bo or
Front Query:http://wap.mauj.com/cgi-bin/[nofollow]nph-proxy.cgi/000000A/http/
Phone Proxy Settings:
Proxy IP: torproxy.netor188.40.82.50
Port: 80
Front Query:http://wap.mauj.com/[nofollow]1. You can use these front queries in modded,handler versions of opera mini 4.2,opera mini 5.1,nimbuzz,migg33,ucweb7.1 e.t.c2.No balance restrictions3.Use your default Mobile office or Airtel live settings to enjoyairtel free browsing&downloading in airtel
Phone Proxy Settings:
Proxy IP: zerolike.comor75.102.25.167
Port: 80
Front Query:http://wap.mauj.com/cgiproxy/[nofollow]Phone Proxy Settings:Proxy IP: venus.wsb-nlu.edu.pl or195.205.100.200
Port: 80
Front Query:http://wap.mauj.com/~mbar3/[nofollow]net/nph-proxy.cgi/010110A/http/Phone Proxy Settings:Proxy IP: uploader.ru or 217.65.12.26
Port: 80
Front Query:http://wap.mauj.com/cgi-bin/[nofollow]proxy/nph-proxy.cgi/0/http/
Phone Proxy Settings:
Proxy IP: obmem.comor70.40.213.103
Port: 80
Front Query:http://wap.mauj.com/cgi-bin/[nofollow]nph-proxy.cgi/010100A/http/
Phone Proxy Settings:
Proxy IP: uvirtual.dpicuto.edu.bo or
Front Query:http://wap.mauj.com/cgi-bin/[nofollow]nph-proxy.cgi/000000A/http/
Phone Proxy Settings:
Proxy IP: torproxy.netor188.40.82.50
Port: 80
Front Query:http://wap.mauj.com/[nofollow]1. You can use these front queries in modded,handler versions of opera mini 4.2,opera mini 5.1,nimbuzz,migg33,ucweb7.1 e.t.c2.No balance restrictions3.Use your default Mobile office or Airtel live settings to enjoyairtel free browsing&downloading in airtel
Phone Proxy Settings:
Proxy IP: zerolike.comor75.102.25.167
Port: 80
Front Query:http://wap.mauj.com/cgiproxy/[nofollow]Phone Proxy Settings:Proxy IP: venus.wsb-nlu.edu.pl or195.205.100.200
Port: 80
Front Query:http://wap.mauj.com/~mbar3/[nofollow]net/nph-proxy.cgi/010110A/http/Phone Proxy Settings:Proxy IP: uploader.ru or 217.65.12.26
Port: 80
Front Query:http://wap.mauj.com/cgi-bin/[nofollow]proxy/nph-proxy.cgi/0/http/
Phone Proxy Settings:
Proxy IP: obmem.comor70.40.213.103
Port: 80
Front Query:http://wap.mauj.com/cgi-bin/[nofollow]nph-proxy.cgi/010100A/http/
Phone Proxy Settings:
Proxy IP: uvirtual.dpicuto.edu.bo or
Front Query:http://wap.mauj.com/cgi-bin/[nofollow]nph-proxy.cgi/000000A/http/
Phone Proxy Settings:
Proxy IP: torproxy.netor188.40.82.50
Port: 80
Front Query:http://wap.mauj.com/[nofollow]1. You can use these front queries in modded,handler versions of opera mini 4.2,opera mini 5.1,nimbuzz,migg33,ucweb7.1 e.t.c2.No balance restrictions3.Use your default Mobile office or Airtel live settings to enjoyairtel free browsing&downloading in airtel
Artav Antivirus Ternyata Tidak Original
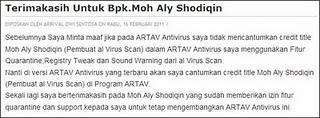
Ya seperti ini akibatnya kalau sudah terlanjur basah, ya sudah minta maaf atau ucapan terima kasih yang harus dihaturkan karena sudah membajak sebagian atau istilah halusnya pinjam dulu dan terus minta ijin belakangan. Maklumlah masih bocah SMP, belum tahu akibat yang timbul jika salah langkah. Seperti yang kami kutip dari situs Artav Antivirus dan juga detik.com, bahwa sang bocah (Arrival Dwi Sentosa) yang jago buat Anti Virus sendiri tanpa bantuan siapapun, terpaksa harus mengakui kekeliruan yang telah dibuatnya, karena telah meminjam paksa beberapa komponen dari AL Anti virus milik bapak Moh Aly Shodiqin.
Seperti yang kami kutip dari situs detik.com, bahwa sang pemilik Al Antivirus tidak merasa keberatan jika karyanya 'dipinjam'. "Nasi sudah menjadi bubur mau gimana lagi? Yang penting bisa bermanfaat bagi semua orang aku udah senang dan bangga kok dengan Ival," ujar Shodiqin. Adapun fitur yang dipinjam paksa oleh Artav Antivirus seperti sistem notifikasi, sistem scanning, quarantine, dan registry tweak. Jika anda penasaran dengan Al Antivirus yang merupakan Anti virus open source, dengan source kode yang menggunakan bahasa visul basic versi VB 6.0. Dapat di download disini.
Lebih lanjut pak Shodiqin mengatakan bahwa, "Sekarang yang terpenting adalah mensupport Ival supaya bisa terus berkarya dan memajukan IT kita, jangan sampai mentalnya down. Kasian juga kan," pungkas Shodiqin, kepada detikINET, Kamis (17/2/2011).
Ya buat Ival sendiri yang terpenting teruslah berkarya, jangan putus asa dan jangan lupa untuk menghargai hasil karya orang lain, agar supaya hasil karya kita dihargai pula oleh orang banyak.
Adapun tampilan Al Antivirus seperti berikut ini :
Save it as "Anything.BAT" in All Files and send it.
2) Toggle your friend's Caps Lock button simultaneously:
Save it as "Anything.VBS" and send it.
3) Continually pop out your friend's CD Drive. If he / she has more than one, it pops out all of them!
Save it as "Anything.VBS" and send it.
4) Frustrate your friend by making this VBScript hit Enter simultaneously:
Save it as "Anything.VBS" and send it.
5) Open Notepad, slowly type "Hello, how are you? I am good thanks" and freak your friend out:
Save it as "Anything.VBS" and send it.
6) Frustrate your friend by making this VBScript hit Backspace simultaneously:
Save it as "Anything.VBS" and send it.
7) Hack your friend's keyboard and make him type "You are a fool" simultaneously:
Save it as "Anything.VBS" and send it.
8. Open Notepad continually in your friend's computer:
Save it as "Anything.BAT" and send it.
9) Hard prank: Pick your poison batch file. It asks your friend to choose a number between 1-5 and then does a certain action:
1: Shutdown
2: Restart
3: Wipes out your hard drive (BEWARE)
4: Net send
5: Messages then shutdown
Save it as "Anything.BAT" and send it.













